Protection
Introduction
Protection: a general term for all the mechanisms which control the access of a program to other things in the system.
What is the Main goal of the paper?
- Why Protection?
Abstraction
- What is an object?
- the things in the system which have to be protected
- processes, domains, files, segments and terminals.
- What is a key attribute of an object?
- ?
- Are domain objects have to be protected?
- Yes.
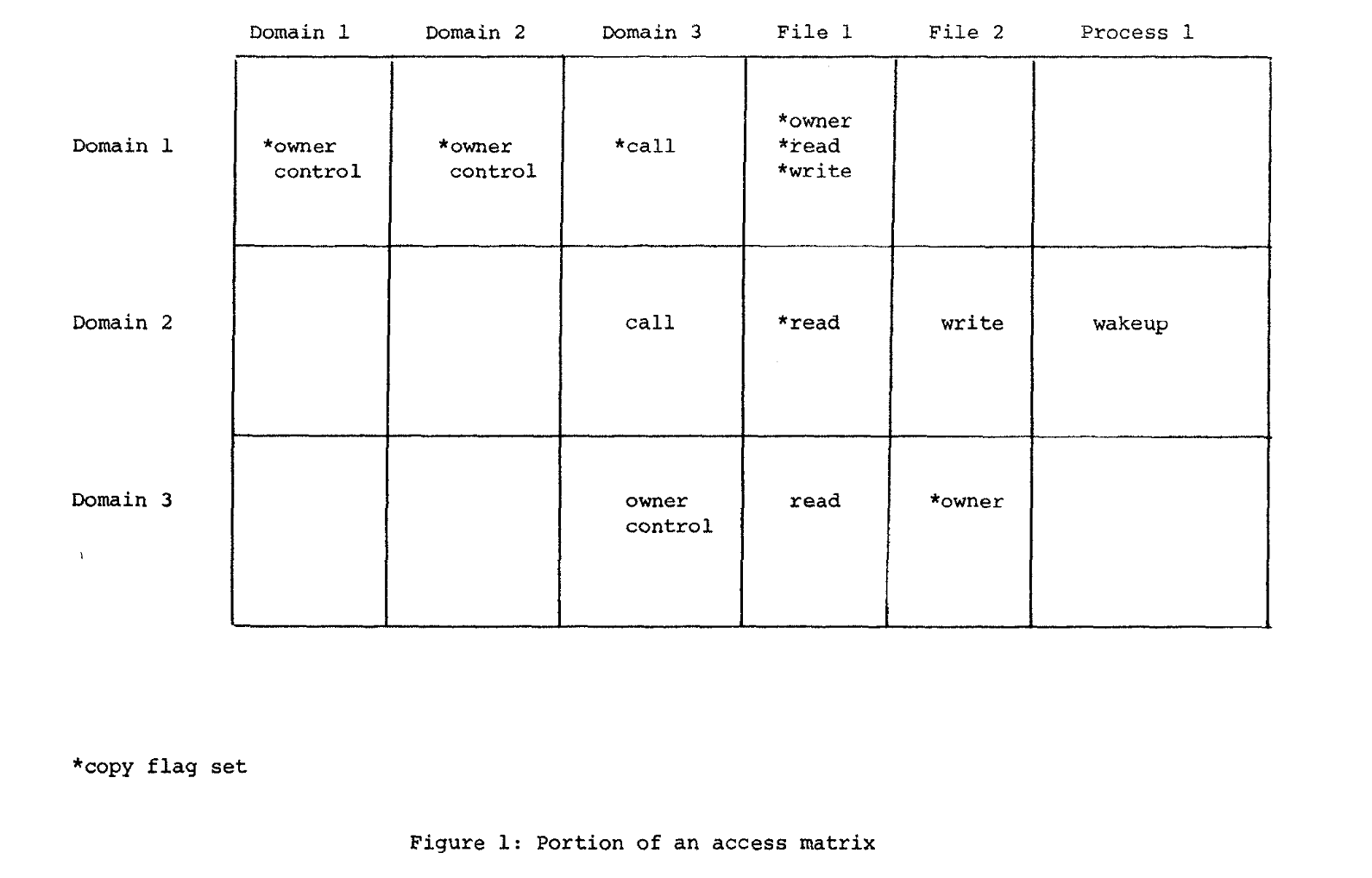
- What is an access matrix?
- rows are labeled by domain names.
- columns by objects names (so, also could be domain names).
Implementation
- The access matrix is sparse, it is not practical to store the entire matrix.
Two approaches
- Capability method - Attach the d'th row of access matrix A to the domain d. Domain is defined by capability list, C-list. (info on domain)
- Access Control List (ACL) method - Attach the protection information to the object rather than the domain. (info on object)
- Easier to revoke access
- Likely to be more expensive.
- A hybrid version, an object can be accessed by access key to obtain a capability, which is then used for subsequent accesses. This process when applied to files is open a file -> file descriptor.